Ransomware, WannaCry and the Problem of Legacy Systems
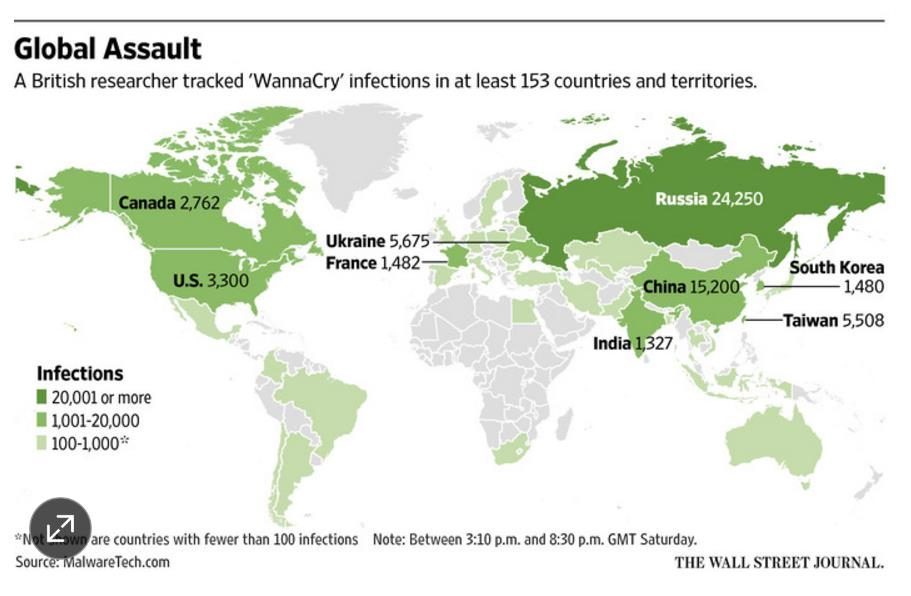
The use of ransomware can be traced back to 1989, with the last peak in attacks recorded in 2013, until this past week. WannaCry has impacted people, companies and governments in more than 150 countries and proven that the ease of deployment plays a role in the rash of security breaches.
At PatchAdvisor, we advise you to keep your operating systems and applications up to date with patches. Without regular attention to system maintenance your systems will remain extremely vulnerable. And, the sheer number of older unpatched/unpatchable computers still in use was proven out across the globe this week. Microsoft Windows XP hadn’t been supported with security patches since 2014, but is still used around the world.
Chris Goggans, the CTO of PatchAdvisor, points out that there are a number of reasons for these older machines to still be in service:
- The organization doesn’t want to spend the money to upgrade to a newer OS.
- The organization is paying for extended support.
- The OS is required for some kind of specialty application.
- The OS is embedded.
Many PatchAdvisor customers find they have all types of legacy systems that won’t work on anything past XP. Applications that manage laboratory devices, for example, need to be certified by external organizations prior to general release, and this can cause a slowing of the upgrade process.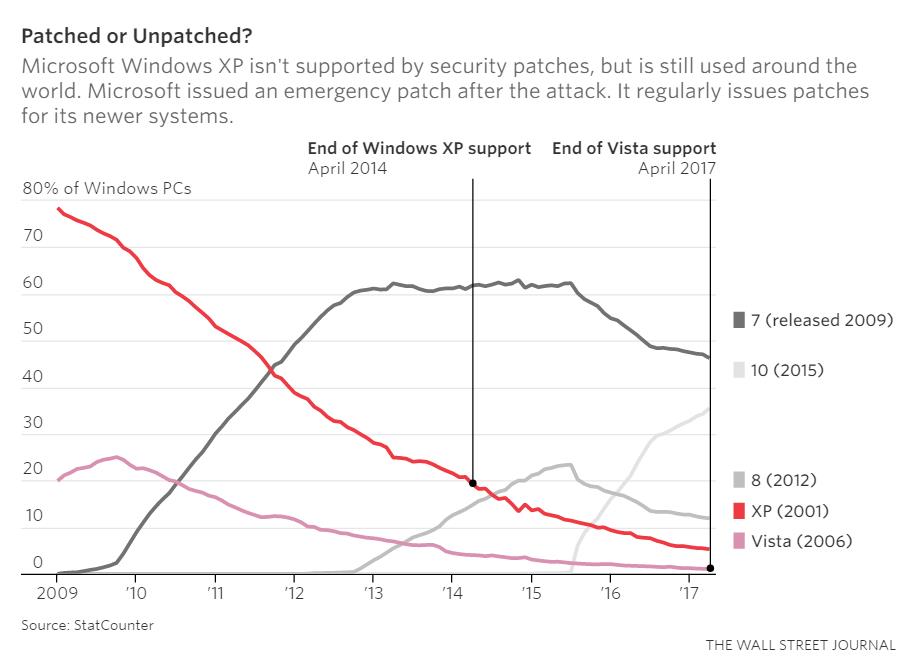
Sometimes the wisdom is in looking at the devices on the network that you do not suspect to be an issue, like printers. Many devices running “XP embedded” have had automatic updates turned off for years because of fears that the updates would affect primary applications. Because of this fear, ATM screens and medical devices took the hit from WannaCry this past week.
At PatchAdvisor, we tell our customers to not expose weak protocols to the Internet, and keep software patched. There’s nothing special in this ‘best practice,’ however it can be difficult to get management to implement, even if logical. If you can’t patch, we suggest segregating your devices and minimize your network traffic to/from them and the rest of the network.
Improving cyber defensive postures for corporations and US government entities has never been more important. In the wake of targeted attacks, and connected computing with the Internet of Things, the projections on the national spend have skyrocketed.
In terms of cyber-attack related damages for enterprises and governments, we anticipate that there will be upwards of $6 trillion through 2022 despite the heavy investment in cybersecurity, according to the Research and Markets, “Global Cybersecurity Market Outlook and Forecasts 2017 – 2022”.
Certain sectors are calling on government and industry groups to take action with their own frameworks outside of the popular NIST approach, including the healthcare sector. Specifically, healthcare professionals, via a recent KLAS-CHIME study, are calling for amendments to the Physician Self-Referral Law (Stark Law) and the Anti-Kickback Statute to allow healthcare organizations to assist physicians with cybersecurity.
Other countries have faced similar discussions. England’s National Health Service has long prepared for the kind of cyberattack that crippled several of its hospitals last Friday. NHS Digital took the step in October 2015 of establishing the Care Computer Emergency Response Team, or CareCERT, an intelligence service that manages national cybersecurity attacks.
With U.S. President Donald Trump’s signing of the cybersecurity order earlier this month, more responsibility is being placed internally in government agencies on departmental secretaries and agency directors to secure digital assets, starting with the use of the NIST framework for risk management.
Particularly critical in the U.S. is the energy grid, and assessing electricity disruption incident response capabilities, as cited in the executive order.
Improving resilience across all global ecosystems is a vaunted goal that requires proactive risk management, including assessing the vulnerability of legacy systems and taking the steps necessary to mitigate those risks. Otherwise, there will be significant breakdowns, like the most recent WannaCry ransomware attacks.


Comments are closed.